Cisco Talos’ Report on UAT-5918 Targeting Critical Infrastructure in Taiwan
What You Should Know
Overview
Cisco Talos has published a highly technical and deeply concerning threat report detailing a malicious campaign by a group it tracks as UAT-5918. The group has been active since at least 2023 and is believed to be aligned with the interests of the People’s Republic of China (PRC), targeting Taiwan’s critical infrastructure through stealthy and persistent intrusion tactics.
This CyberSec Taiwan Report Insight summarizes the core findings of the Cisco Talos report in strategic terms, presenting eight targeted takeaways that connect the technical evidence to larger themes in Taiwan’s cyber defense posture and regional security dynamics.
1. UAT-5918 Is Building Long-Term Access, Not Causing Short-Term Disruption
This group is not launching ransomware or defacing websites. Instead, it is silently burrowing into critical networks to maintain persistent access. Its objective is information theft and long-term positioning, likely in preparation for potential geopolitical escalation.
Why It Matters: This activity reflects the strategic use of cyberspace as a domain for peacetime preparation. By embedding in critical systems during non-conflict periods, adversaries gain the ability to disrupt or paralyze infrastructure quickly if tensions escalate. For policymakers, this reinforces the need to treat persistent access campaigns as part of broader strategic competition, not isolated technical incidents.
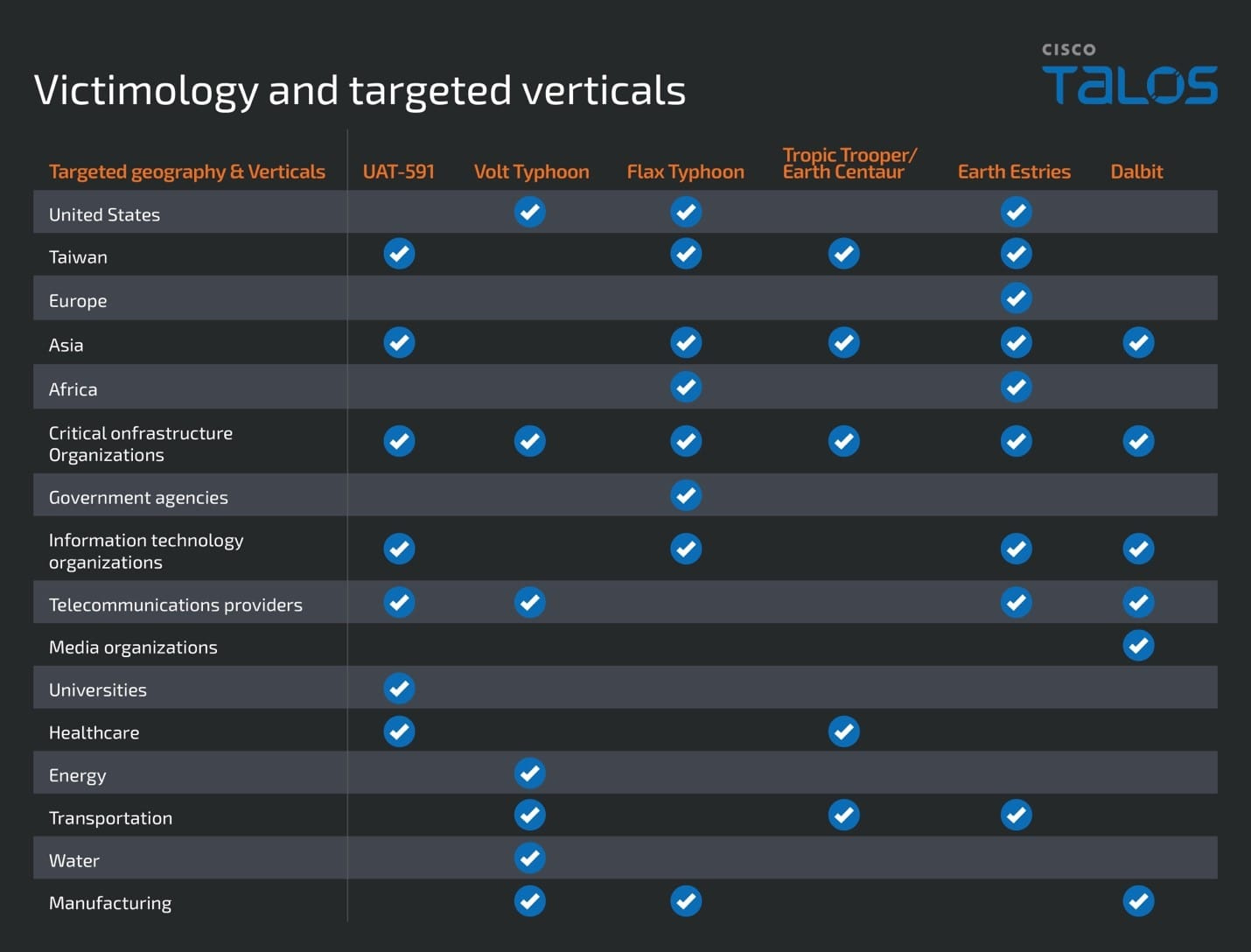
2. Taiwan’s Critical Sectors Are Squarely in the Crosshairs
UAT-5918 is targeting telecommunications, healthcare, IT service providers, and other high-value infrastructure in Taiwan. These are sectors where disruption would have severe cascading effects across society and national security.
Why It Matters: These sectors are essential to both daily stability and emergency response. Their compromise in a conflict scenario would dramatically reduce Taiwan’s ability to communicate, treat its population, or coordinate defense. This targeting pattern should shape how Taiwan prioritizes investments in resilience and how allies tailor their support.
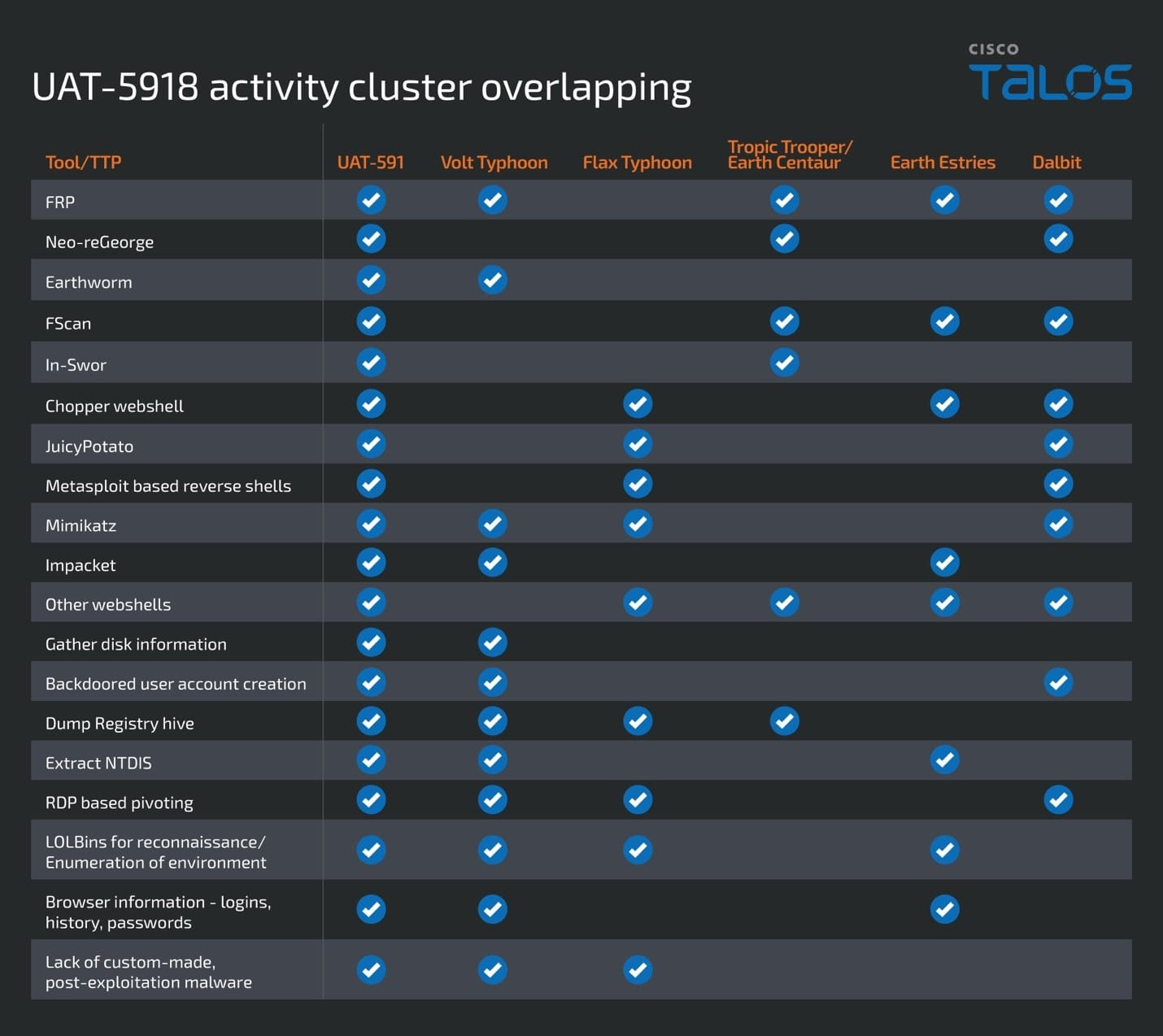
3. The Group Uses Public Tools, Not Custom Malware
UAT-5918 relies heavily on living-off-the-land techniques: publicly available web shells, red-team tools, and built-in Windows utilities.
Why It Matters: The use of non-attributable, widely available tools is a deliberate choice to avoid detection and attribution. This raises policy challenges around threat identification and legal response, complicating international coordination and signaling. It also reinforces the need for capabilities focused on behavioral detection and anomaly-based monitoring.
4. There Are Clear Overlaps with Other PRC-Linked Groups
UAT-5918 shares tactics and tooling with Volt Typhoon, Flax Typhoon, Dalbit, Earth Estries, and Tropic Trooper.
Why It Matters: The overlap points to a coordinated strategy, not just opportunistic targeting. Taiwan is likely facing a multipronged campaign designed to diversify points of access and reduce detection risk. Policymakers must consider these intrusions in aggregate as part of a state-directed approach to shaping outcomes in the Taiwan Strait.
5. Initial Access Is Achieved via N-Day Vulnerabilities
Rather than using zero-day exploits, UAT-5918 leverages known but unpatched vulnerabilities in publicly exposed infrastructure.
Why It Matters: This reinforces that low-cost, scalable tactics remain effective against high-value targets. It also underscores the gap between policy intention and operational implementation of cybersecurity practices. Governments must incentivize and support rapid patching, particularly across critical sectors and legacy systems.
6. Credential Harvesting and Admin Account Creation Are Standard Procedure
The group escalates access by harvesting credentials and creating administrator accounts.
Why It Matters: This enables long-term persistence and lateral movement without triggering alarms. It illustrates how gaps in identity and access management can be exploited for strategic control. Policymakers should consider mandating stronger authentication, logging, and anomaly detection standards across infrastructure providers.
7. Post-Compromise Behavior Is Manual and Adaptive
The group’s actions are highly manual and customized, adapting in real time to each network environment.
Why It Matters: This level of operational discipline suggests a well-resourced and mission-driven actor. It also points to the strategic intent to remain undetected for extended periods. National cyber defense strategies should prepare not just for noisy attacks but for low-and-slow compromises that may only be detected through advanced threat hunting.
8. Taiwan Is a Testing Ground for Global Tactics
Some tools and techniques in this campaign appear to be used for the first time, while others reflect previously observed activity in campaigns against the United States and other democratic states.
Why It Matters: Taiwan is once again serving as an early target environment for adversary experimentation. This gives Taiwan’s defenders unique visibility into threat evolution. It also presents an opportunity for partners to collaborate with Taiwan on intelligence sharing and joint analysis, turning Taiwan’s frontline status into a collective advantage.
Final Thought: This Is a Policy Challenge, Not Just a Technical One
UAT-5918’s activity is not an isolated campaign but a reflection of a broader strategic doctrine. It is part of a growing pattern of pre-positioning activity designed to degrade infrastructure trust, complicate crisis response, and shape the outcome of potential future conflict.
Taiwan and its partners must move beyond reactive threat response and invest in forward-looking detection capacity, real-time intelligence exchange, and regulatory frameworks that reduce systemic risk. This includes clear expectations for patching, account auditing, and network segmentation across critical sectors.
This report reinforces the reality that cyber intrusions are better understood not as discrete technical events but as recurring features of adversarial components of a long-term geopolitical strategy. Taiwan’s resilience depends on sustained policy attention, cross-sector coordination, and an acknowledgment that cyber campaigns are now embedded in the fabric of strategic competition.
Read the full report.
CyberSec Taiwan
About CyberSec Taiwan
Your source for the latest news and analysis on Taiwan-centric cybersecurity.
The CyberSec Taiwan Substack account is not affiliated with iThome or its annual CYBERSEC conference in Taiwan.