Incident Overview
In a data breach incident that continues to unfold, Taiwan's largest telecom company, Chunghwa Telecom, fell victim to a substantial cyber attack. Initial reports of this incident surfaced on March 1, revealing that hackers, allegedly backed by the Chinese government, infiltrated Chunghwa's systems and stole approximately 1.7TB of company data. This stolen data, including military documents and government contracts, was subsequently put up for sale on a dark web marketplace.
The National Defense Ministry of Taiwan has since confirmed the breach, stating that the compromised information encompassed documents from various government departments, including the armed forces, foreign affairs ministry, and coast guard. Importantly, the ministry emphasized that no confidential information was compromised during the breach, offering some relief to the incident.
Analysis
Taiwan, being one of the prime targets for cyber attacks worldwide, has faced a persistent and sophisticated threat landscape. Government authorities have characterized much of the ongoing cyber threats as a manifestation of persistent "gray zone harassment" perpetrated by China, which occurs nearly daily. These actions include provocative maneuvers such as flying warplanes around the island and dispatching vessels to its surrounding waters. Although these tactics fall short of overt acts of war, analysts suggest they are sufficient to keep Taiwan's military and cybersecurity agencies preoccupied.
Notably, Microsoft has recently highlighted the activities of a China-based threat group named Flax Typhoon, which targeted Taiwanese organizations. According to the tech giant, Flax Typhoon's objectives include conducting espionage operations and maintaining long-term access to various Taiwanese entities.
As further details emerge on the Chunghwa Telecom data breach, experts are increasingly drawing attention to the broader trends concerning dark web actors from China, who use the same or similar tactics, techniques, and procedures (TTPs) as Flax Typhoon and other state-sponsored threat groups to steal data.
However, it is critical to understand that attribution in cyberattacks can be very difficult and are commonly not named without sufficient evidence. There remains a possibility that this attack, and the perpetrators, could be non-state actors, working to support the efforts of the Chinese government, but not necessarily in an official capacity. This shroud of anonymity and plausible deniability is of course one of the advantages state actors maintain.
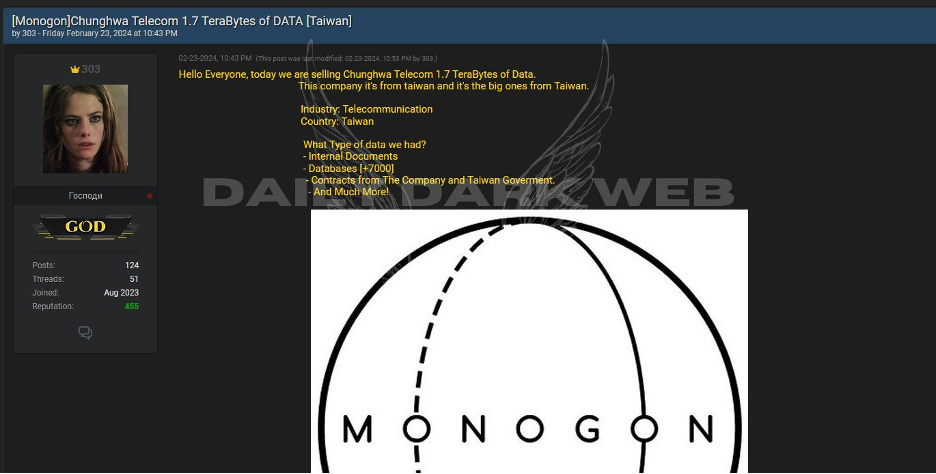
It is also important to note that while threat actors have posted the stolen Chunghwa Telecom data for sale on a dark web marketplace, authenticity of this sale has not yet been validated. Meaning, at this point, it has not been made public that the posted sale is legitimate. While credibility is another form of currency leveraged by threat actors on the dark, there is also the risk of disingenuous advertising or transaction. This determination and interaction with the seller is typically not made public, due to its sensitivity and the financial and public image that may impact the victim, Chunghwa Telecom in this case. This facilitation is, or likely already has been, carried out between the seller and, most likely, a third party incident response or dark web specialist vendor contracted and acting on behalf of the victim.
To learn more about the intricate relationship between China and Taiwan on the dark web, DarkOwl published a comprehensive report in 2022, examining the increased dark web activity between China and Taiwan, shedding light on the digital underground's response and the impact of recent cyberattacks on Taiwan's political landscape. Additionally, in 2023 CyberInt released their report on recent crackdowns to Western dark web forums by government agencies, potentially prompting threat actors to shift focus to Chinese-speaking platforms, and explores the rivalry between leading Chinese underground forums Deepmix and Chang’an.
Outlook
The short and long-term impacts of this breach on Chunghwa Telecom's operations and reputation remain uncertain, as the investigation into the incident is still ongoing. However, this incident underscores the industry-wide trend of escalating cyber threats, signaling the critical need for organizations to proactively invest in cybersecurity to mitigate risks and limit potential fallout.
In response to this breach, Taiwanese officials have urged Chunghwa Telecom to strengthen its information security controls to prevent similar incidents in the future.
Over the past decade, Chunghwa Telecom has demonstrated its dedication to increasing the security of customer data through various initiatives. These measures include the establishment of its subsidiary, CHT Security, a leading Managed Security Service Provider (MSSP) in Taiwan, as well as a partnership with Trend Micro in 2019 to introduce a new mobile Internet of Things (IoT) security service. However, there is a lack of evidence regarding Chunghwa Telecom's internal efforts to safeguard its own systems, raising concerns about the effectiveness of their internal protections.
The breach at Chunghwa Telecom serves as a stark reminder of the significant challenges faced by large organizations in responding to cyber threats and investing in data protection. It highlights the urgency for such organizations to develop robust defensive measures and remain vigilant in the face of increasingly sophisticated attacks, as well as reinforces the critical imperative for proactive cybersecurity investments.
We will report more on this incident as new and relevant information is provided.
CyberSec Taiwan
About CyberSec Taiwan
Your source for the latest news and analysis on Taiwan-centric cybersecurity.







